Case Study - The Target Breach – You Are Only as Secure as Your Partners Are
Background
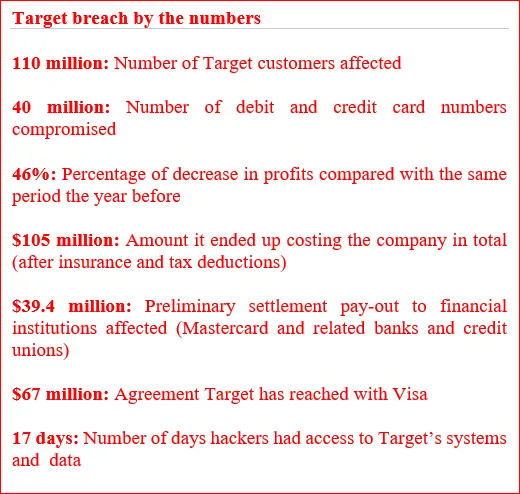
In late-November 2013, Target Corporation’s (Target), one of the largest retail companies in the United States, security and payment system was breached. Attackers gained access to Target’s computer network, stole the financial and personal information of as many as 110 million Target customers, and then removed this sensitive information from Target’s network to a server in Eastern Europe. As a result, over 40 million credit and debit card numbers were compromised, along with 70 million addresses, phone numbers and other personal information. In addition, once inside Target’s network, the attackers were able to gain direct and complete access to every single cash register in every Target store.

Security Lapses
Attackers were able to gain access to Target’s network through HVAC company Fazio Mechanical Services, a third-party vendor, Target gave network access to. Fazio Mechanical Services is a refrigeration, heating and air conditioning subcontractor that has worked at a number of locations at Target and other top retailers. The third-party vendor did not appear to follow broadly accepted information security practices and Target’s network credentials were gathered after one of Fazio’s employees fell victim to a phishing scheme attack and clicked on a malicious email. However, Fazio is not to be entirely blamed for the breach, Target failed to implement proper network segmentation to protect their servers, as a result the attackers were able to penetrate through.
Learning Points
Importance of supplier management
What many companies fail to understand is that, cyber security isn’t only isolated to your company and data systems. Not only is your firm’s security crucial, your fellow partners must be protected as well. Any vendor, so long as it has a link or assess to your firm’s data, is a potential entrance point for a breach. Target learnt this the hard way. It is the same principle as safe driving. It only requires one single driver to not abide by the rules for an accident to occur, even if everyone else abides with all the safety procedures and precautions.
Proper network segmentation and protection practices
This is a lesson in network protection and segmentation. Had Target employed proper network segmentation practices and followed up to ensure that practices were followed for all its partners, attackers wouldn’t have been able to leverage on the third-party access to gain a foothold in Target’s network.
In addition, Target failed to properly isolate its most sensitive network assets, as a result, the attackers were able to move from less sensitive areas of Target’s network to systems storing confidential consumer data.
In the unfortunate event that a breach has occurred, it is crucial to contain the breach and isolate it and prevent attackers from assessing other parts of the system. There needs to be walls and layers of protection between systems.
Activity monitoring and incompetence of security team
Target was actually prepared in terms of cyber security. In fact, in May 3013, a $1.6 million malware detection software by high profile computer security firm FireEye (whose companies include CIA and Pentagon) was installed. A FireEye team monitored Target’s system around the clock and reported the activity to Target’s security team. However, the FireEye’s feature of eradicating malware was turned off as mistrusted by Target security personnel.
Finally, on November 30, the FireEye team eventually sensed that something was amiss, when attackers installed exfiltration malware to move stolen information out of the Target servers. FireEye team notified Target’s security team accordingly. However, for some unknown reasons, Target’s security team failed to act on the alert, allowing customer information to be compromised.
In addition, Target’s security team also failed to respond to multiple automated warnings from the company’s anti-intrusion software that the attackers were installing malware on Target’s system and multiple warnings from the company’s anti-intrusion software regarding the escape routes the attackers planned to use to exfiltrate data from the network.
All in all, the incompetency of Target’s IT security personnel can be clearly seen.
Aftermath
Impaired firm reputation
Target was hit with over 90 lawsuits related to the massive data breach. The brand plummeted from #7 to #21, out of the top 10, as the “best-perceived brand among consumers”. Also, Target’s CSR score – a measure of the enterprise dimensions of reputation that include ‘workplace,’ ‘governance,’ and ‘citizenship’ – fell dramatically as well, the largest drop among any US retail company in the same time frame.
Stock value slides
The stock experienced a 10% drop in price in the aftermath of the security breach.
Dismissal of staff and internal instability
In January 2014, two months after the breach, Target lays off 475 employees at its headquarters in Minneapolis and worldwide and leaves another 700 positions unfilled.
Enjoyed this article? Curious to find out how you can better protect your organisation, data systems and critical accounts in the event of a cyber-attack? Contact us now for an in-depth consultation to obtain cyber security measures best tailored for your needs. CyberForSec® team will work with your employees, train and guide them in adopting the appropriate cyber security skills in their work processes.

References:
https://www.commerce.senate.gov/services/files/24d3c229-4f2f-405d-b8db-a3a67f183883
https://browse.arxiv.org/pdf/1701.04940.pdf
https://medium.com/@rithikvgopal/complete-case-study-target-data-breach-2-ba4bb365a82e
By Alvin Lam Wee Wah
and Team at CyberForSec.
Interested in what you've read and want to know more or collaborate with us? Contact us at customersuccess[a]cyberforsec.com replacing the [a] with @.