Unveiling the Anatomy of Hacking: How to Defend Against Intruders
In today's interconnected world, the digital realm is a treasure trove of information and opportunities. However, it's also a battlefield where hackers are constantly on the prowl, searching for vulnerabilities to exploit. Understanding their methods is the first step in fortifying your defenses.

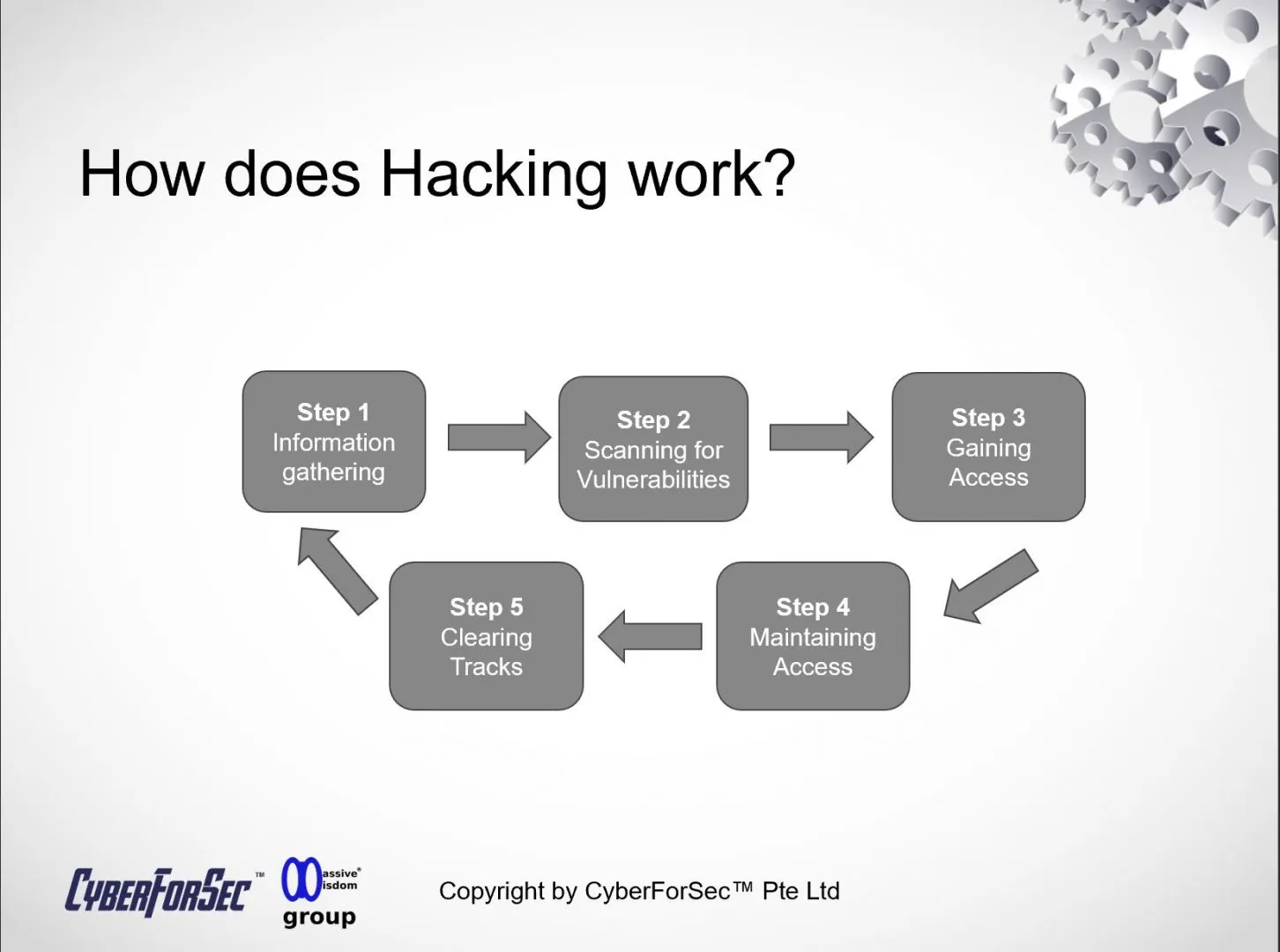
1. Information Gathering: Hacking doesn't start with a grand heist; it begins quietly with information gathering. Hackers employ various techniques to collect data about their targets. This can include scouring social media profiles, utilizing publicly available information, and even engaging in spear-phishing campaigns to extract sensitive data like login credentials or personal information.
2. Scanning for Vulnerabilities: Armed with information, hackers move on to scanning networks and systems for vulnerabilities. They use automated tools to identify weaknesses, misconfigurations, or outdated software that could serve as potential entry points. Vulnerabilities can range from unpatched software to weak passwords or open ports.
3. Gaining Access: Once a vulnerability is identified, the hacker attempts to exploit it. This can involve various attack vectors, such as deploying malware, executing code injection attacks, or leveraging social engineering tactics. Successful exploitation grants them unauthorized access to systems or networks.
4. Maintaining Access: Hackers aim to maintain their access undetected. They might create backdoors, establish persistence mechanisms, or compromise privileged accounts to ensure they can return at will. This stage is critical for their long-term objectives, which could include data theft, espionage, or launching further attacks.
5. Clearing Tracks: As they move deeper into the compromised environment, hackers want to cover their tracks. They erase logs, alter timestamps, and take steps to ensure that their presence remains undetectable. This makes it challenging for cybersecurity professionals to trace their activities.
Now that we've unveiled the hacker's playbook, let's talk about how to defend against these threats effectively:
- Strengthen Your Cyber Hygiene: Regularly update your software, employ strong, unique passwords, and be cautious about sharing personal information online. Educate your team about cybersecurity best practices within your organization.
- Employ Robust Security Solutions: Invest in comprehensive cybersecurity tools, including firewalls, intrusion detection systems, and antivirus software. These can help detect and prevent various stages of an attack.
- User Training and Awareness: Train your employees to recognize phishing attempts, social engineering tactics, and other common attack vectors. An educated workforce is a powerful defense.
- Monitoring and Incident Response: Implement continuous monitoring to detect suspicious activities early. Develop an incident response plan to contain and mitigate potential breaches promptly.
- Regular Penetration Testing: Periodically assess your systems and networks through penetration testing. Identifying vulnerabilities before hackers do allows you to patch and fortify your defenses.
- Seek Expert Guidance: Consider partnering with cybersecurity experts who can provide tailored solutions, threat intelligence, and 24/7 monitoring to protect your digital assets.
Join us in our comprehensive exploration of hacking's inner workings on the Cyberforsec Blog. In our upcoming detailed blog post, we'll provide actionable tips and best practices to help you safeguard your digital assets, whether you're an individual or an organization. Your cybersecurity is our priority, and we're here to empower you with the knowledge and tools to protect yourself from cyber threats effectively. Stay tuned!
By Alvin Lam Wee Wah
and Team at CyberForSec.
Interested in what you've read and want to know more or collaborate with us? Contact us at customersuccess[a]cyberforsec.com replacing the [a] with @.